One of the core purposes of Continuous Security Validation (CSV) is to ensure that the security controls are configured as hermetically as possible to confirm that it is both preventing unwanted intrusions and enabling unfettered operations.
Misconfigured security controls are the source of 65-70% of all security issues in the cloud, and Gartner estimates that 99% of firewall breaches through 2023 will result from misconfiguration, a sobering reminder of the crucial importance of keeping security controls shipshape.
Fine-Tuning Existing Security Controls
In this context, the term security controls, though limited to the digital infrastructure,
still covers any parameters implemented to protect data or assets in any form and the
organization’s infrastructure as a whole.
With such a wide-ranging definition, no wonder some security controls are misconfigured.
The advent of agile development resulted in the constant creation of new sets of parameters
to configure and check. Appropriately setting the number of security controls to oversee
and manage is fast exceeding the limits of what can be humanely expected from the IT team
already drowning under requests for patching vulnerabilities added to their task list.
Three steps are required to ensure a sound security control configuration
• The first step is to properly configure all security controls is to identify those that
need to be fine-tuned.
• The second step is to prioritize the reconfiguring of the faulty security controls.
• The last step is to perform the fine-tuning, but only after ensuring that a
configuration modification is operationally safe, meaning that tightening the
configuration will not hamper the smooth running of the application or other
operation.
Given the substantial number of security controls, automating the detection of
potentially exploitable ones, and grading them according to the risk they pose saves a
considerable amount of time and optimizes the efficiency level.
This can be done either manually using the MITRE ATT&CK framework or using automated
continuous security validation solutions that operationalize the MITRE framework.
Taking Advantage of the MITRE ATT&CK Framework
MITRE ATT&CK is an open-source project collating all known vulnerabilities and mapping the known tactics, techniques and procedures (TTPs) used by malicious actors within an infrastructure to escalate their attack, reach the crown jewels, and perform actions such as exfiltrating data, encrypting and blocking access to all or part of the environment, divert computing resources, or otherwise disrupt or destroy.
The MITRE framework covers fourteen tactics, a few hundred techniques and an ever-growing number of procedures.
The tactics are presented as columns containing the techniques used for each tactic. The procedure part can be visualized by selecting a specific vulnerability from the MITRE database Entering that vulnerability in the database will light up all the techniques used for that vulnerability, across the tactics. This can be color-coded according to security scores and other parameters.
Manual use of the MITRE ATT&CK framework is resource-intensive, cumbersome, and sometimes too slow to be of use, but different solutions have emerged to operationalize the MITRE framework, effectively making it available for all.
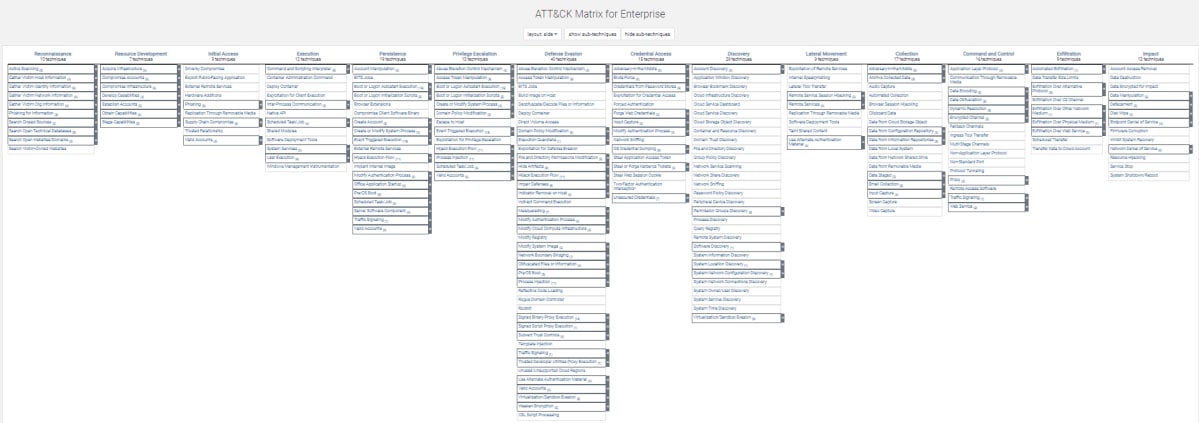
MITRE’s 14 Tactics are:
• Reconnaissance: information gathering to strategize future adversary operations
• Resource Development: obtaining, hijacking, or creating resources to support malicious operations
• Initial Access: any attempt to penetrate the network or infrastructure – the most popular being phishing with various degrees of sophistication
• Execution: any attempt to run malicious code within your network or infrastructure
• Persistence: any attempt to solidify an unauthorized foothold
• Privilege Escalation: any attempt to obtain higher-level permissions
• Defense Evasion: any attempt to avoid being detected
• Credential Access: any attempt to appropriate accounts names and passwords
• Discovery: any attempt to understand your environment or network through exploration
• Lateral Movement: any attempt to move within your environment
• Collection: any attempt to gather data that can be leveraged to further the attack
• Command and Control: any attempt to communicate with compromised systems and control them
• Exfiltration: any attempt to steal data by transferring it outside the environment
• Impact: any attempt to manipulate, interrupt, or destroy systems and data
Using solutions that operationalize the MITRE ATT&CK Framework is highly effective in detecting APTs and in taking preventative action to prevent successful escalation.
Scaling Up Security Control Validation
Manually validating security controls based on detection tools is rapidly becoming an overwhelming task as your environment grows. Rapid deployment and CI/CD pipelines that have become the norm are already taxing IT teams resources.
The result of this recent DevOps paradigm, the COVID 19 related rapid and unplanned massive migration to work from home and the general migration to cloud-based infrastructure, hybrid or native, has resulted in exponential growth of the number of security controls to configure, validate and monitor.
At the same time, access to malicious offensive tools has grown exponentially, enabling potential cyber-criminals to run advanced attacks with limited technical knowledge, simply by using automated attack tools requiring little to no configuration.
The only viable way to maintain a stable security posture without increasing staff proportionally to the growth of security control is to adopt offensive testing techniques aimed at tracking openings in the security infrastructure that could be used by potential attackers.
Fortunately, cyber defenders have developed a few of these tools such as:
• Attack Surface Management (ASM)
• Breach and Attack Simulation (BAS)
• Continuous Automated Red Team (CART)
• Purple Teaming (PT)
Each of these tools can be added individually to your cybersecurity tool stack, depending on your needs and resources. To extend your security posture management capability to its maximum extend, incorporating at least ASM and BAS to start with, and adding CART and PT as your resources grow, is the recommended strategy.
To minimize the required resources to leverage those tools, whenever possible, select a vendor offering all options in a single-pane-of-glass dashboard, which will facilitate scaling up as needed.
